Cybersecurity & Backup
Phishing: How to Spot a Fraudulent Email

Example of a Phishing Email
Below is an email that appears completely legitimate. It asks a user to take a mandatory anti-spam test before a certain date. It is sent with the logo of a reputable company, uses familiar formatting, and its purpose seems justified. Other seemingly reasonable motives may be invoked, such as suspension of service due to unpaid invoices or (one of our favorites!) an intrusion alert on one of your accounts followed by a request to log in for verification to avoid account suspension.
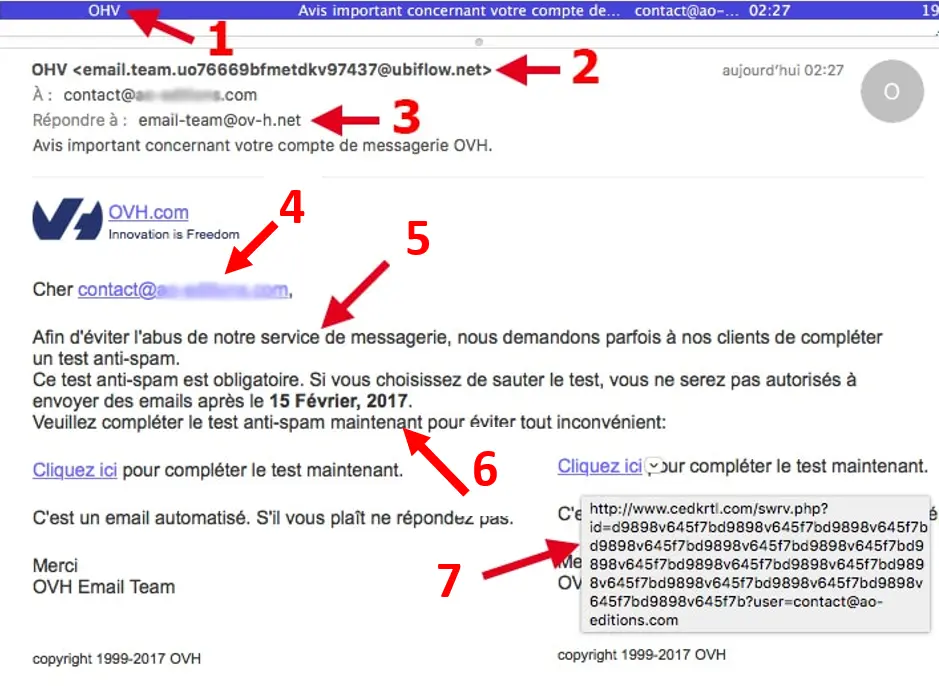
Let’s take the didactic example above to analyze its content. Several signs clearly indicate a phishing attempt:
- A typo in the title or the body of the text, which is poorly written;
- The sender is identified as “OVH”, but upon closer inspection, the sender’s email address is rather strange, with a domain name ending in ‘@ublifow.net’. This attempt is quite crude, but often the sender address is extremely similar to a legitimate domain—one letter off, a ‘.net’ instead of a ‘.fr’, etc.;
- The reply-to email address also uses a suspicious domain name: ‘@ov-h.net’;
- The greeting is addressed not to your name or first name, but to an email address. Similarly, greetings that are overly generic can raise suspicion;
- The text in the body of the email contains strange syntax or appears poorly translated;
- The message urges you to act quickly and/or highlights negative consequences if you do not. The goal is to pressure you so you overlook other warning signs;
- The redirect link in the email may look legitimate, but if you hover your cursor over it, the real redirect URL will appear, and not only will it be different, but it will often look highly suspicious;
- This is not the case in this email, but if it contains an attachment, never open it—especially if the attachment’s title piques your curiosity. That is intentional and likely indicates malware.
Another situation requiring vigilance is when the sender uses the “sent as” function. This allows an email to appear as if it comes from a legitimate address, such as ‘@amadeus.com’ shown in red below.

The real sender’s email is the one shown in green on the right. In this example it is clearly visible, but sometimes you need to hover your mouse over the email—WITHOUT clicking—to reveal the true sender.
Finally, other common-sense rules apply. For example, if you are not typically the recipient of this type of email, or if the message requests unusual or critical actions, you should be cautious. When in doubt, ask your colleagues or your IT manager.
Example of a Fake Phishing Website
If you have nonetheless clicked such a link, you will likely land on a page that looks just like a legitimate website. Criminals copy the layout down to the smallest details. However, if you take a closer look at the example below—which recently appeared in the press—you will notice that the URL (website address) is not that of the government, since the ‘.app’ sequence should not be there.
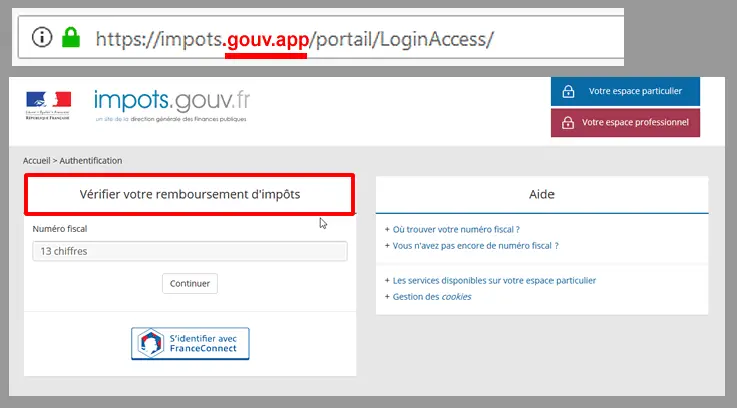
If you think it would have been difficult to notice, that means the fraud was well executed. Indeed, it is unlikely that most of us know the exact web address of the tax administration website by heart and could distinguish the real one from the fake. What should you do in such cases? If you are unsure, it is recommended to connect directly to the site (via a Google search or your bookmarks, for example) rather than clicking on the redirect link included in the email.
MAG.
Wi-Fi & Network
Cybersecurity & Backup
Video Surveillance & Security
Consulting
IT Managed Services
Cybersecurity & Backup

Cybersecurity & Backup
Ransomware: How to Protect Yourself from Cyberattacks
Ransomware: what it is and why it is dangerous In simple terms, ransomware are computer viruses ...
+
+

Cybersecurity & Backup
How to transition to remote work?
Forms and solutions for remote work Remote work doesn't look the same across companies. Depending ...
+
+
Your hotel deserves IT excellence
Let's discuss your challenges, whether you're in the hospitality sector or an SME.